Late one evening last week, deep within the Imperial Palace on Coruscant, a handful of officials gathered around a circular obsidian table. They were not there to plan a conquest or unveil a superweapon. They were there to autopsy a catastrophe.
Spread before them were pages of a leaked internal report detailing how the Rebel Alliance managed to steal the Death Star plans. It was a breach so embarrassing that the Empire’s top brass initially tried to vaporize all evidence of it, Scarif base included. Grand Moff Tarkin’s chair sat ominously empty, but his specter loomed in the form of scathing margin notes he left on the draft prior to his sudden demise at Yavin.
Officially, Imperial spokespeople maintain that the Death Star was lost to Rebel "sabotage." Unofficially, the files tell a different story. The destruction of the Empire’s billion-credit battle station was not the result of Rebel bravery. It was the result of preventable governance failures, ignored audit findings, and a culture that treated data security as an afterthought.
Identity Management: The "Liana Hallik" Incident
The report’s first section reveals a lapse that would be comical if the stakes weren't planetary. Jyn Erso, the Rebel ringleader, had been an Imperial prisoner under a fake name weeks before the heist.
Despite being the daughter of Galen Erso, the project’s chief architect, Imperial Intelligence failed to realize who she was. She sat in a labor camp cell under the alias “Liana Hallik.” According to the audit, a simple cross-database check correlating the alias with known associates of the Erso family would have exposed her immediately. Instead, Alliance commandos waltzed into the Wobani labor camp and “rescued” the prisoner in a chaotic shootout. The Empire was not even aware it had held the key conspirator in its grasp until she was already gone.

Access Controls: The "Ocean" Defense
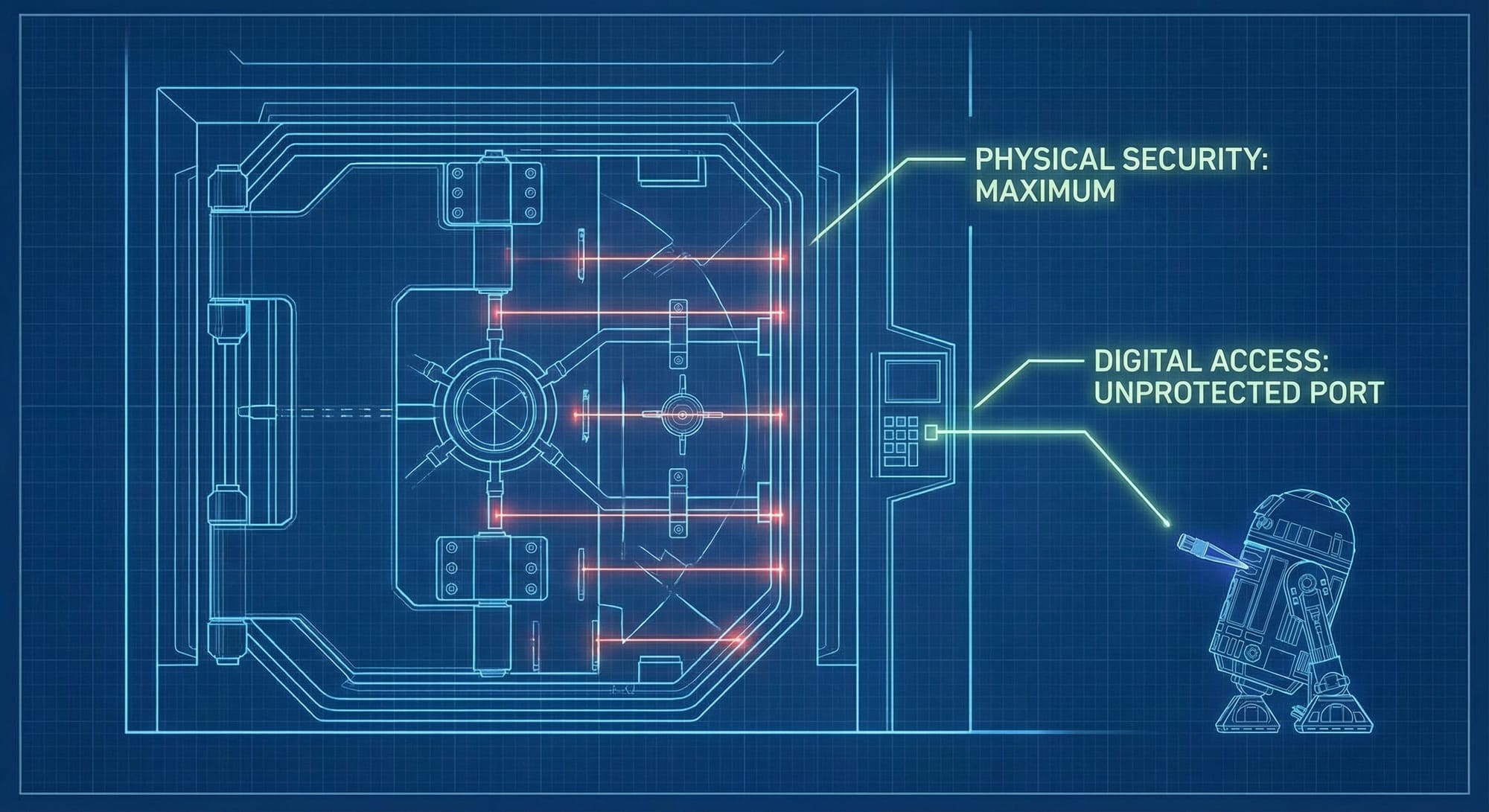
The technical schematics themselves were protected by physical might but digital negligence. One internal audit noted that the Scarif data vault, which housed the only complete copy of the schematics, did not employ multi-factor access controls.
“We had vault guards, a planetary shield, and an ocean on the outside, sure,” says a former Imperial security analyst on condition of anonymity. “But once you got past that, the internal network was a free-for-all. There was nothing to stop you from walking out with whatever you wanted.”
The system relied on "perimeter defense," a classic cybersecurity blunder. When the Rebels struck, posing as Imperial security staff, the Citadel Tower data vault accepted them without a query. There was no biometric challenge. There were no real-time behavior analytics. A single droid plugged into a terminal and the system treated it like routine maintenance.
The Insider Threat
Perhaps the most damning finding concerns the project’s Chief Engineer, Galen Erso.
Unbeknownst to his superiors, Erso embedded a thermal exhaust port vulnerability into the station’s design. It was a flaw so specific it practically invited a proton torpedo. The audit concludes that basic peer review or an independent code audit could have detected this sabotage years ago.
However, the top brass placed unquestioning trust in Erso, amplified by the siloed nature of the project. Director Orson Krennic notoriously warned his team to cease “excessive concern with hypothetical vulnerabilities,” creating a culture where questioning the code was tantamount to treason. With one man holding unchecked authority over the design, the stage was set for betrayal. It was a classic "Key Person Risk," ignored because the person in question was "too important to audit."

The Absurd Remediation
In the halls of power, the reckoning has been swift. Several senior commanders have been executed for “allowing” the leak. Imperial HR has yet to comment on this particular retention strategy.
But the true moment of absurdist reckoning came during a high-level strategy meeting this Tuesday. A young ISB analyst suggested hiring outside consultants to test Imperial systems, specifically "white hat" hackers with Rebel expertise. The room reportedly went silent until Darth Vader’s breathing cut through the air.
“We have already paid a high price for the Rebels’ consulting,” he noted.
Instead, the Empire has opted for a more traditional corporate response. Memos went out this morning requiring mandatory cybersecurity awareness holovids for all staff. The new curriculum includes a forty-minute module titled "Is It Phishing or Is It a Jedi Mind Trick? Verifying Requests from Hooded Visitors."
Employees must score 80% or higher on the quiz to regain door access privileges—because the Empire may possess world-ending power, but it was brought to its knees because nobody bothered to encrypt the file named "Stardust."






